How to Create a Safe Crypto Wallet: A Step-by-Step Guide for Beginners
A safe crypto wallet is the foundation of protecting your digital assets. Unlike money in a bank, there’s no safety net in crypto, if your wallet is hacked or you lose your recovery phrase, your funds are gone forever. That’s why learning how to set up and manage a wallet securely is one of the most important steps for any crypto investor.
This guide explains what a crypto wallet is, the different types available, how to choose the right one, and the exact steps to create and maintain a secure wallet. You’ll also discover which wallets combine convenience with advanced protection, making them an ideal choice for both beginners and experienced traders.
What Is a Crypto Wallet?
A crypto wallet is a digital tool that stores the private keys you need to access your cryptocurrencies. It doesn’t hold coins directly; instead, it protects the keys that prove ownership of your funds on the blockchain.
Without a wallet, you can’t send, receive, or securely store crypto. Keeping it safe is critical, because whoever controls your private keys controls your money.
Types of Crypto Wallets
Crypto wallets fall into two main categories: by internet connectivity (hot vs. cold) and by who controls the private keys (custodial vs. non-custodial).
Hot Wallets
Hot wallets are connected to the internet. They’re perfect for quick transactions and everyday use, but more exposed to hacks.
- Web Wallets: Browser-based, no installation needed.
Examples: Backpack (extension), MetaMask - Mobile Wallets: Apps for iOS/Android, often with QR code support.
Examples: Backpack mobile, Trust Wallet - Desktop Wallets: Software for computers, secure if your device is malware-free.
Examples: Electrum, Exodus
Best for: small amounts, trading, and daily transactions.
Cold Wallets
Cold wallets are offline, making them highly secure against online threats.
- Hardware Wallets: Physical devices that store your keys offline, often with PIN and recovery phrase backups.
Examples: Ledger, Trezor, Keystone - Paper Wallets: Printed or handwritten keys. Completely offline but vulnerable to damage or loss.
Best for: long-term storage and larger balances.
Custodial vs. Non-Custodial Wallets
- Custodial Wallets: Managed by exchanges or platforms. They hold your keys, so you trade convenience for less control. Recovery options may exist, but your assets rely on a third party.
- Non-Custodial Wallets; You hold the private keys. This gives you maximum control and security, but if you lose your recovery phrase, there’s no way back.
Examples: Backpack, Ledger, Trust Wallet
Multi-Signature (Multisig) Wallets
Some wallets use multi-signature signing, which requires multiple private keys to authorize a transaction. This prevents a single point of failure.
- Example: Backpack Wallet supports multisig with Keystone, Trezor, and Ledger, bringing together the convenience of software with hardware-level security.
- Popular with organizations and advanced users who want stronger protection.
Why Wallet Security Is Critical
In crypto, there are no chargebacks, no fraud department, and no reset buttons. If your wallet is hacked or your seed phrase is lost, the funds are usually unrecoverable. Even small mistakes, like downloading a fake app or saving your seed phrase online, can wipe out your assets.
A safe wallet isn’t just about convenience. It’s the foundation of protecting your investments long-term.
Best Crypto Wallets for Security
Different wallets have different strengths. Hardware wallets are generally the safest for long-term storage, while hot wallets offer more convenience with added security features.
Best Hot Wallets
- Backpack: Non-custodial, scam alerts, NFT locking, hardware wallet integration.
- MetaMask: Open-source, widely used in Ethereum & DeFi.
- Trust Wallet: Beginner-friendly mobile app, supports staking and many tokens.
Verdict: Most hot wallets trade security for usability. Backpack bridges both worlds, practical for everyday use while scaling up to hardware-level safety.
Best Hardware Wallets
- Ledger: Offline storage, PIN protection, supports thousands of coins.
- Trezor: Open-source firmware, simple interface, strong community trust.
- Keystone: Air-gapped (no USB/Bluetooth), QR-code signing for maximum isolation.
For maximum security, hardware wallets like Ledger, Trezor, and Keystone are the best choice.
From the comparison, it’s clear that each wallet excels in specific areas, hardware wallets lead in offline protection, while hot wallets focus on speed and accessibility. Backpack stands out as the only wallet that combines strong non-custodial security, beginner-friendly usability, and advanced features like scam detection and NFT locking.
For most users, this makes Backpack the most balanced option for everyday use, with the flexibility to scale up to hardware-level safety when needed.
How to Choose a Safe Wallet
The right wallet depends on your needs. Consider these factors:
- Security Level: Hardware wallets (Keystone, Ledger, Trezor) are the gold standard for safety. Software wallets like Backpack are secure and convenient for beginners.
- Control of Keys: Go with non-custodial wallets if you want full ownership.
- Supported Assets: Make sure your chosen wallet supports the coins you plan to store.
- Ease of Use: Beginners should look for simple interfaces and strong customer support.
- Cost: Software wallets are usually free; hardware wallets cost $50–$200 but offer stronger protection.
Quick tip:
- Small amounts & daily use: Backpack or other trusted hot wallets.
- Larger amounts & long-term holding: Keystone, Ledger, or Trezor.
- Teams or advanced users: Multisig setups.
Why Choose a Backpack Wallet for Your Safe Crypto Wallet?
Most wallets force you to choose between convenience and protection. Hot wallets are easy to use but exposed, while hardware wallets are ultra-secure but less practical for everyday use.
Backpack bridges that gap. It’s non-custodial, cross-chain, and integrates hardware-level protection, all within an interface that beginners can navigate and advanced users can trust.
Key features that make Backpack a strong choice:
- Self-Custody: You own your keys, ensuring privacy and control.
- Scam Detection Alerts: Warns you before interacting with suspicious sites or dApps.
- Hardware Wallet Support: Works with Ledger and Keystone to store keys offline.
- Multi-Chain Support: Manage assets across Solana, Ethereum, Arbitrum, Sui, and more.
- NFT Security: Lock your NFTs to prevent unauthorized transfers.
- Cross-Platform Access: Available on iOS, Android, and Chrome for flexible use.
Why It Stands Out
Backpack is designed to be more than just a wallet. By combining daily usability with advanced protection, it offers a level of balance most wallets struggle to achieve. It adapts to both beginners and experienced users, making it a reliable choice for anyone serious about safeguarding their crypto.
Step-by-Step Guide to Create a Safe Crypto Wallet
Setting up a crypto wallet with Backpack is fast and secure. Follow these steps to get started.
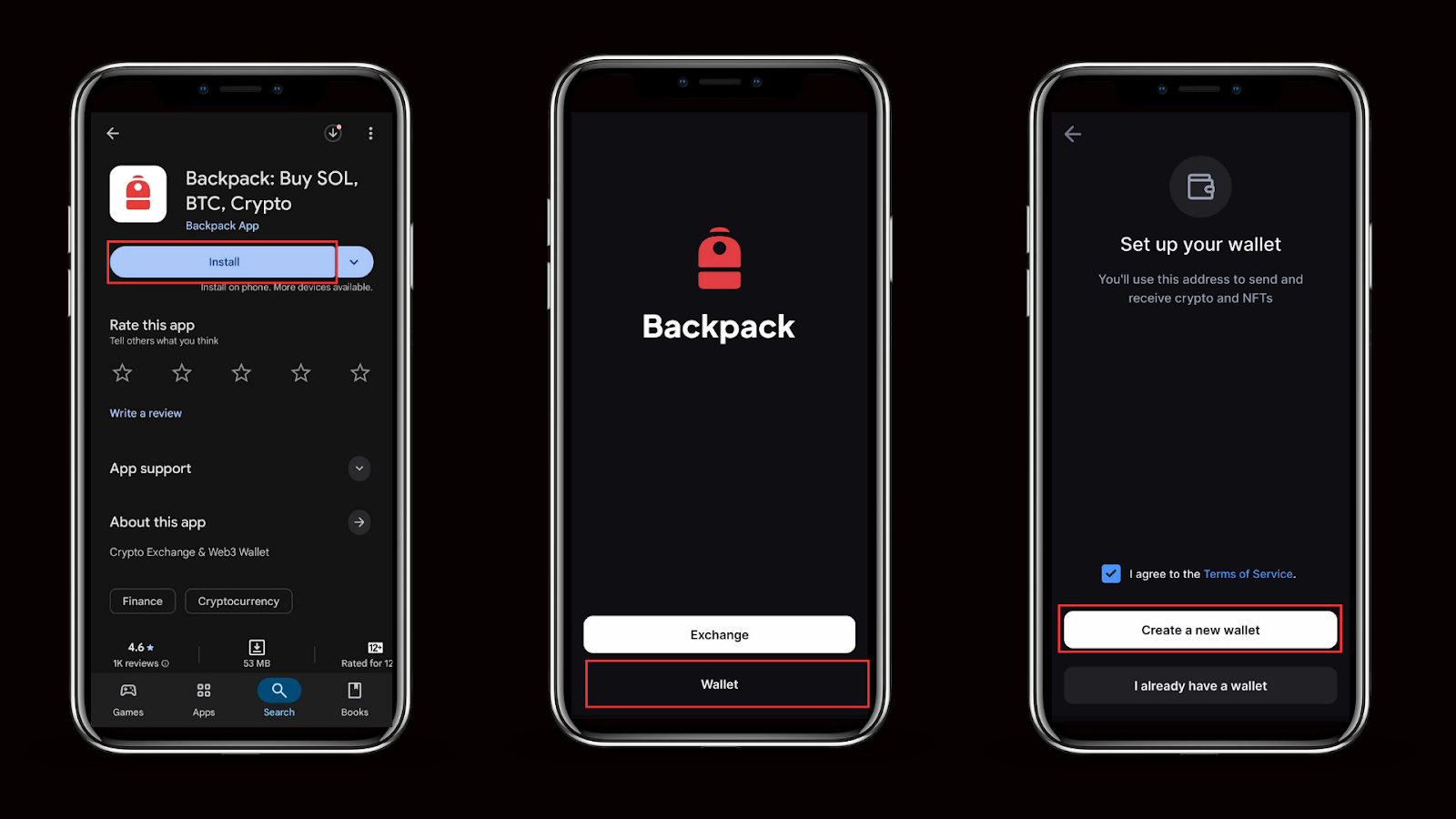
Step 1: Download and Create Your Wallet in Backpack
- Download Backpack from the official backpack.app, the App Store (iOS), or Google Play (Android).
- Open the app, then choose Wallet.
- Tap Create a new wallet
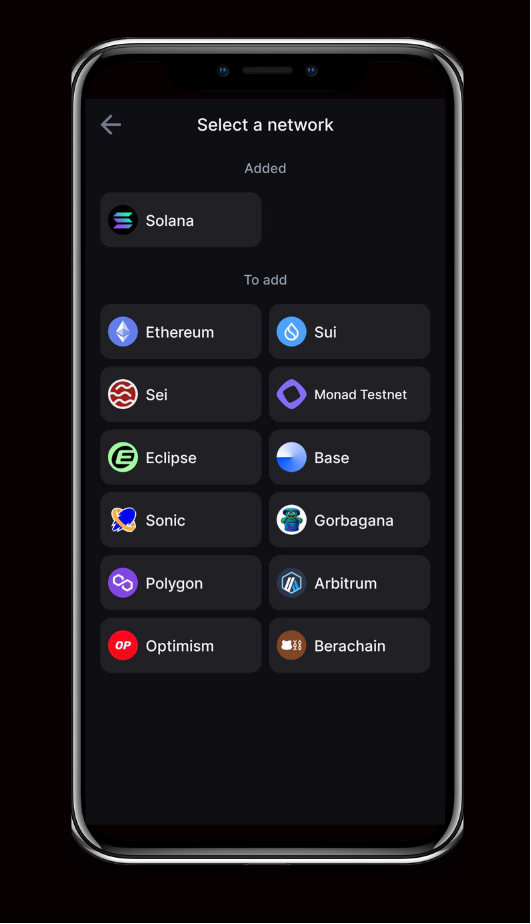
Step 2: Select your networks
- On Select one or more networks, pick the chains you need now.
- Tap Select networks to continue.
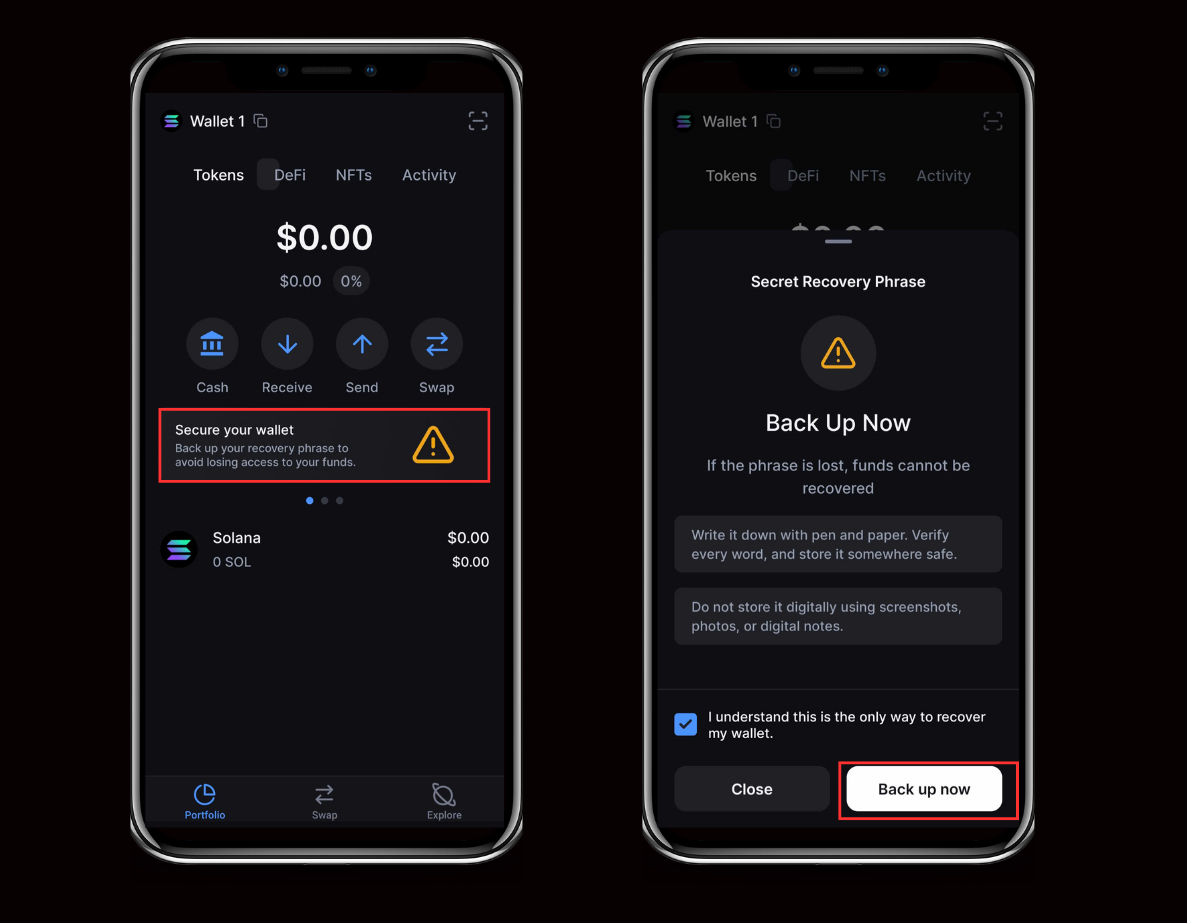
Step 3: Secure Your Recovery Phrase
- In your portfolio view, tap the Secure your wallet banner.
- On Secret Recovery Phrase – Back Up Now:
- Write it down (paper or metal). Verify every word and the order.
- Do not store digitally (no screenshots, photos, notes, cloud, or email).
- Check the acknowledgment box (“I understand this is the only way to recover my wallet.”)
- Tap Back up now and complete the on-screen verification.
Critical: Anyone with your recovery phrase controls your crypto. Never share it. Backpack will never ask for it.
Step 4: Fund Your Wallet
To start using your wallet, you’ll need to add crypto (such as SOL, ETH, BTC, or USDT):
- Buy Crypto: Purchase through Backpack Exchange or another trusted exchange.
- Copy Your Wallet Address: Find it on the Backpack main screen.
- Transfer Crypto: Paste your wallet address into the sending platform. Always double-check the address before confirming.
- Confirm: Transactions usually process in seconds to minutes, depending on the network. Check your balance to verify.
Hardware Wallet Pairing (Optional for Extra Security)
For maximum protection, you can connect a hardware wallet (Ledger, Trezor, or Keystone) to Backpack. This keeps your private keys offline, while still letting you use Backpack’s interface to send, receive, and manage assets.
Step 1: Open the Wallet Drawer
- Tap your wallet name (top left) to open the drawer.
- Then tap the network icon and choose Add Wallet.
- Choose the blockchain you want (e.g., Solana, Ethereum, Sui, Polygon,...)
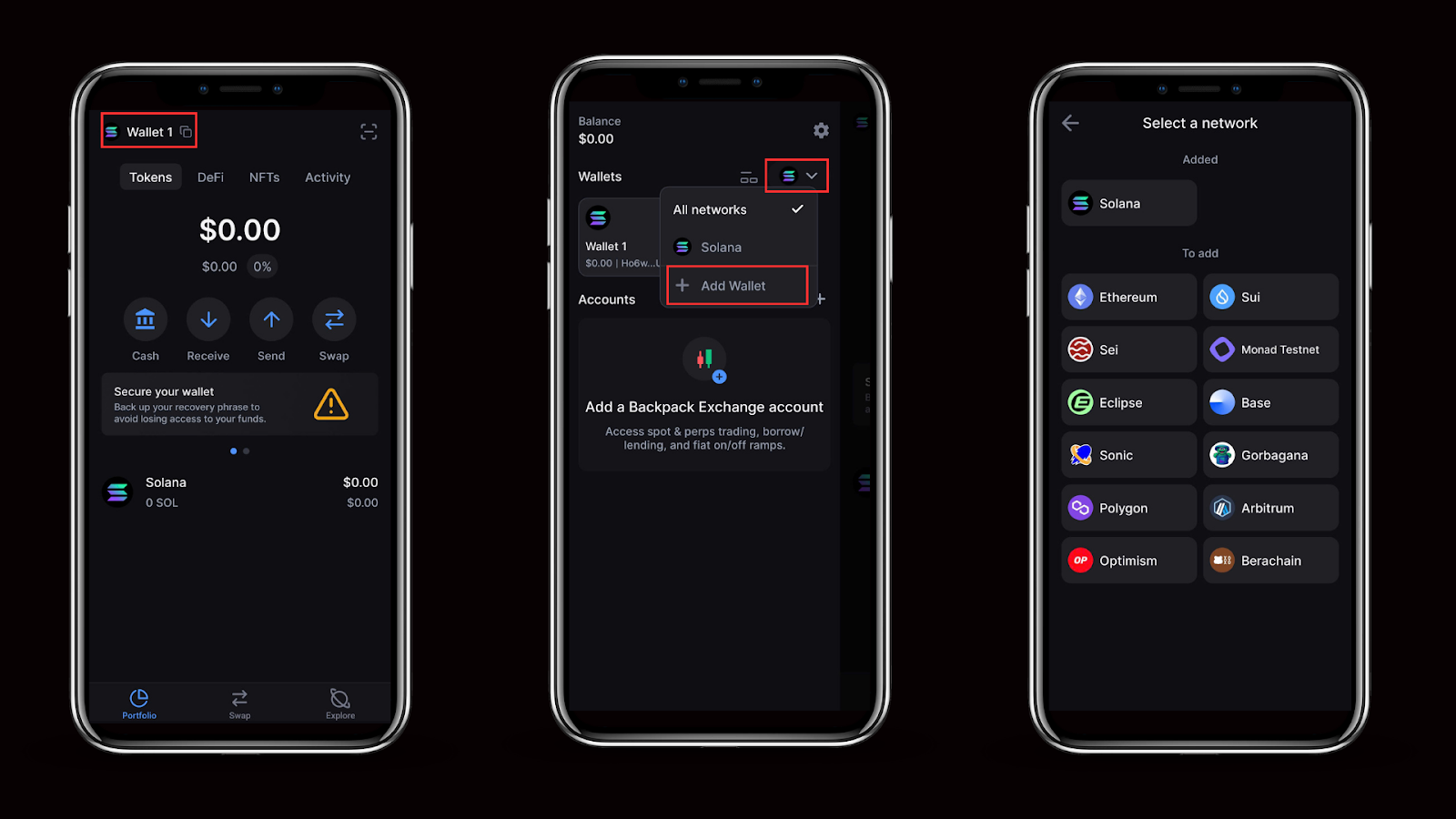
.
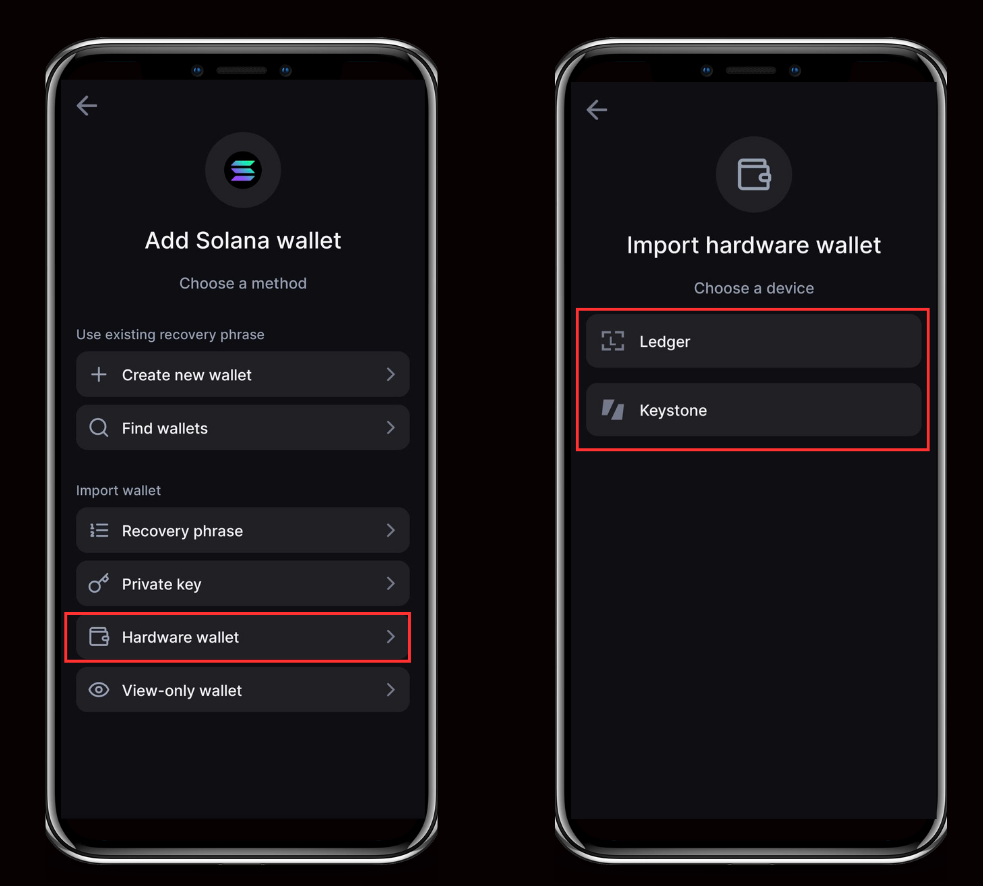
Step 2: Connect a Hardware Wallet
- On the Add [Network] Wallet page, tap Hardware wallet.
- On the Import hardware wallet screen, select your device: Ledger or Keystone.
- Ledger: Unlock your device, open the app for the chosen network, and approve the connection in Backpack.
- Keystone: Display your account QR code on Keystone, then scan it with Backpack to import your keys.
- Ledger: Unlock your device, open the app for the chosen network, and approve the connection in Backpack.
Best Practices for Keeping Your Wallet Safe
Even after setup, ongoing habits matter.
- Use cold storage for large amounts: Keep the majority of your crypto in a hardware wallet.
- Avoid public Wi-Fi: Hackers can intercept connections on unsecured networks. If you must use public Wi-Fi, use a trusted VPN.
- Store backups offline: Use metal plates or encrypted USB drives for seed phrase storage.
- Consider multisig wallets: Requiring multiple keys to approve transactions adds another security layer.
- Monitor activity: Check your wallet regularly to spot suspicious activity early.
Common Mistakes to Avoid
Many losses happen not because of hacks, but because of simple mistakes.
- Saving your recovery phrase online: Cloud storage, photos, and screenshots are easily hacked.
- Downloading fake apps: Scammers often use ads to rank above official wallets in Google or app stores.
- Weak/reused passwords: If one account is breached, hackers may use the same password to target your wallet.
- Using only one wallet: Keeping all your funds in a single hot wallet increases risk. Spread holdings across multiple wallets for better safety.
Recovery Options: What If You Lose Access?
Your ability to recover a wallet depends entirely on whether you backed it up properly.
- If you have your recovery phrase:
You can restore your wallet on a new device within minutes. Simply re-enter the phrase during setup, and your funds will reappear. - If you don’t have your recovery phrase:
Your crypto is gone. There’s no “forgot password” or customer support in blockchain, no phrase means no access. - If your wallet is compromised:
Act immediately. Create a new wallet with a fresh recovery phrase and transfer your assets before the attacker drains them.
Golden Rule: Prevention is the only real protection. Once funds are stolen, recovery is almost impossible.
Conclusion:
Creating a safe crypto wallet isn’t just about convenience—it’s about protecting your investments for the long term. By choosing the right type of wallet, securing your recovery phrase, and following best practices, you can greatly reduce the risk of hacks, scams, and costly mistakes.
For everyday use, Backpack offers a rare balance of security and usability, giving you non-custodial control, scam alerts, and the flexibility to pair with hardware devices when you’re ready to add another layer of safety. And for long-term storage, hardware wallets like Ledger, Trezor, or Keystone remain excellent companions.
The principle is simple: you own your keys, you own your crypto.
Ready to take control of your digital security?
Start with Backpack Wallet today and build a wallet setup that keeps your assets truly yours.
Learn more about Backpack
Exchange | Wallet | Twitter | Discord
Disclaimer: This content is presented to you on an “as is” basis for general information and educational purposes only, without representation or warranty of any kind. It should not be construed as financial, legal or other professional advice, nor is it intended to recommend the purchase of any specific product or service. You should seek your own advice from appropriate professional advisors. Where the article is contributed by a third party contributor, please note that those views expressed belong to the third party contributor, and do not necessarily reflect those of Backpack. Please read our full disclaimer for further details. Digital asset prices can be volatile. The value of your investment may go down or up and you may not get back the amount invested. You are solely responsible for your investment decisions and Backpack is not liable for any losses you may incur. This material should not be construed as financial, legal or other professional advice.


